Did you know that 71% of organizations have ongoing application security problems, and nearly half of them – 46% – have persistent bugs classified as their most critical security risks? In practice, this situation is a ticking time bomb, posing a serious challenge to the organization. Whether you’re a programmer, system administrator, or security manager, understanding these OWASP security vulnerabilities is essential to protect yourself from cyber-attacks.
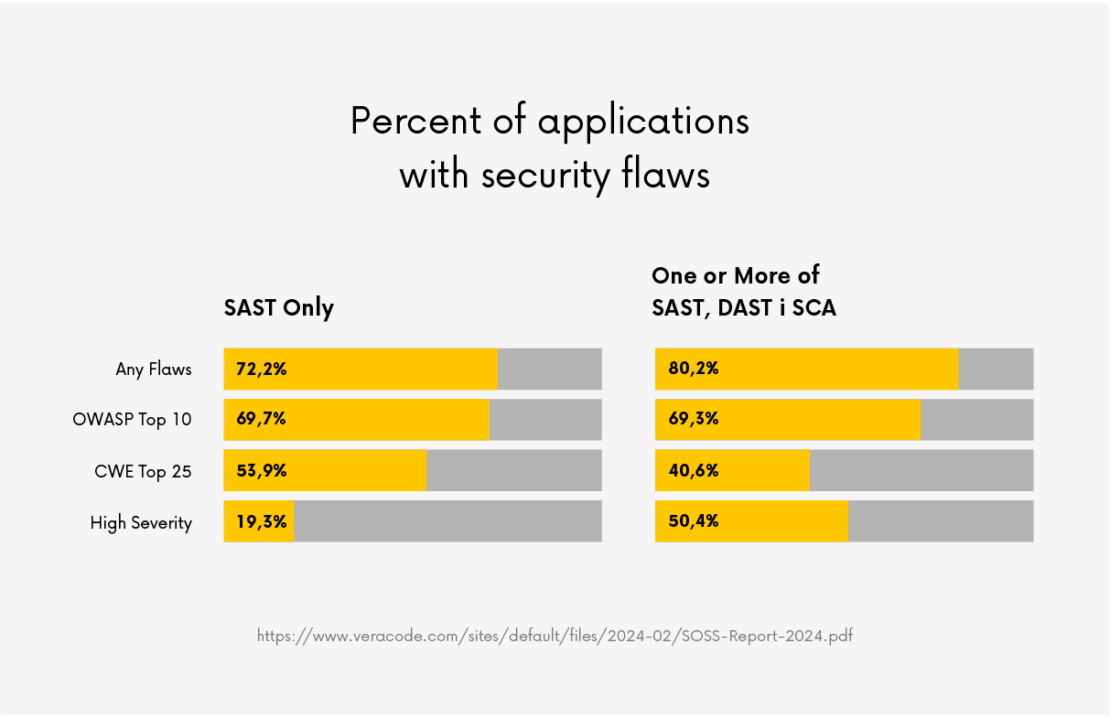
As technology evolves, web application security risks are increasing. As you can see in the graphic below, 70% of applications have bugs included in the OWASP Top 10, an initiative to track the most critical threats to web applications.
For the Common Weakness Enumeration (CWE) Top 25 – another initiative to track the most common and influential security vulnerabilities – that statistic drops slightly to 41% of all applications. According to Veracode’s February 2024 report assessment, half of applications have flaws considered high (or very high).
This just goes to illustrate that with the number of cyberattacks on the rise and the cost of attacks running into the millions, protecting your software and data integrity from breaches should be the number one concern for companies of all sizes. In this article, we’ll take a closer look at the most common application security threats discussed in OWASP’s Top 10 reports and how to prevent them.
Table of Contents
What is OWASP, and why was it created?
OWASP (Open Web Application Security Project) is an international non-profit organization dedicated to improving web application security. Founded in 2001, it has more than 32,000 volunteers from around the world and provides its security resources, such as tool documentation, videos, and forums, free of charge. OWASP’s most recognizable product is the OWASP Top 10 project, a regularly updated report that outlines the top ten security threats to web applications.
When learning about the OWASP Top 10, we must remember that, of course, this list is not exhaustive of all possible software security threats. Rather, its purpose is to highlight the most critical web application security threats, providing a starting point for software and security experts and professionals.

Why is the OWASP Top 10 important?
Understanding OWASP guidelines and standards helps developers update their knowledge of common vulnerabilities and threats so they can secure code that can reduce the risk of vulnerabilities in their applications. By following defensive programming rules and OWASP guidelines, developers write secure code, that reduces the likelihood of security breaches in all software development lifecycle. This security-conscious approach not only protects their applications but also builds customer trust, a key factor in today’s digital age where data breaches are commonplace.
OWASP is also recognized as the industry standard for web application security, which commits to best practices for secure software development. The OWASP Top 10 list is also often used as a benchmark for security auditors and analysts. Failure to address security vulnerabilities can signal problems reflected in an organization’s overall security status.
How often is the OWASP Top 10 updated?
Since 2003, OWASP has updated the Top 10 list every three to four years, reflecting changes and advances in application security. The rankings are based entirely on contemporary research and opinions gathered from the global community of cybersecurity professionals. The most recent update was in 2021, highlighting new security vulnerabilities and threats that have emerged over time.
Below you can see the changes in the OWASP Top 10 from 2017 and 2021.
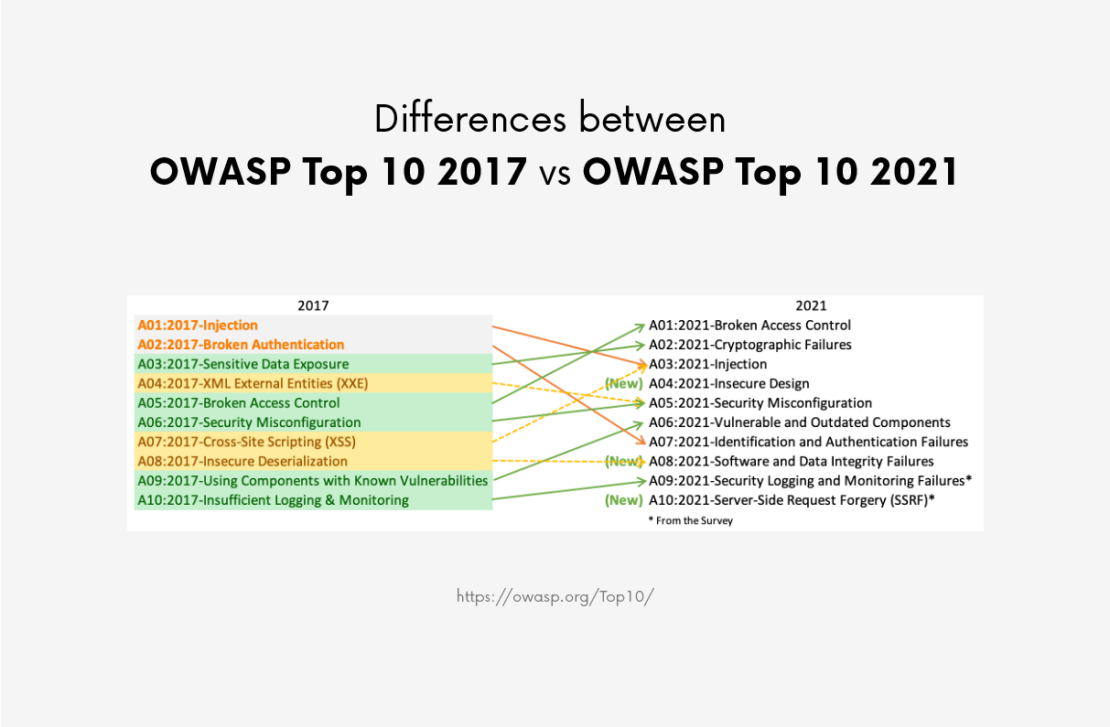
There are three new categories, four of which have been renamed and changed in scope. They focus on the causes of ataxia, not just the symptoms.
Explanation of the most critical security risks
The OWASP Top 10 identifies and explains the most prevalent network security threats, providing insight into known vulnerabilities and how attackers exploit them.
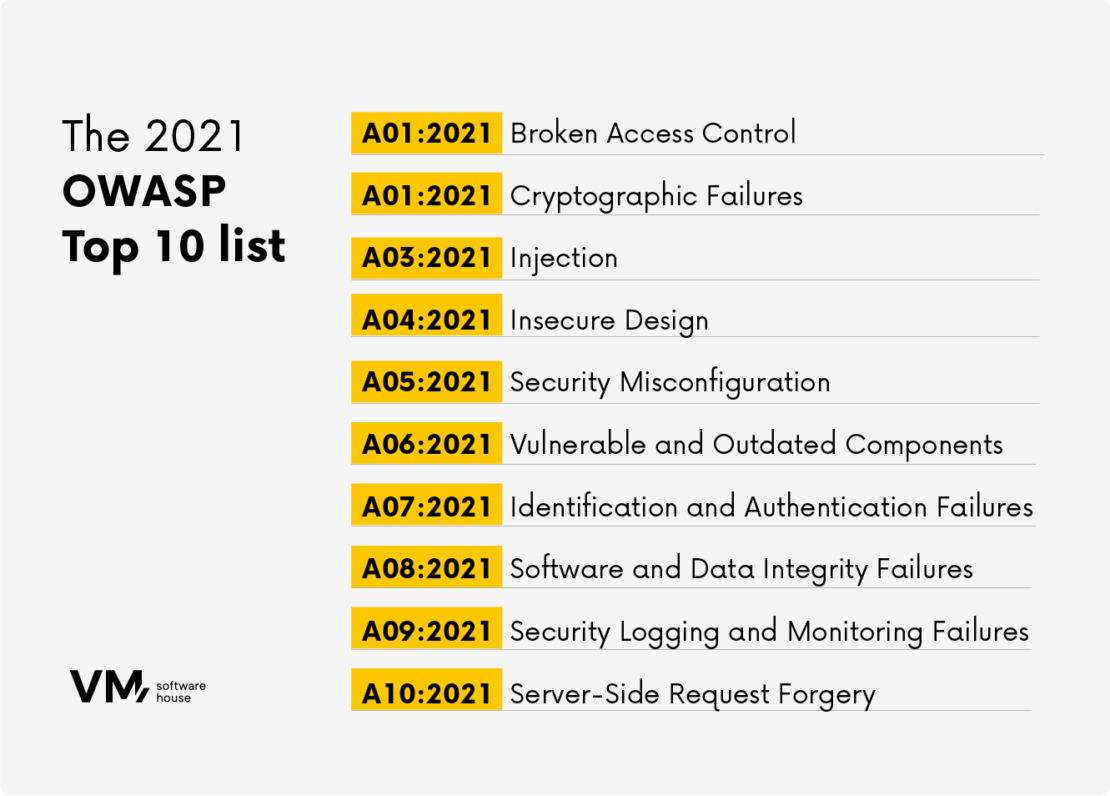
A01:2021-Broken Access Control
Broken access control security vulnerabilities occur when we do not adequately enforce restrictions on what actions authenticated users can perform. Attackers exploit these vulnerabilities to gain unauthorized access to sensitive functions, data, or resources.
How do we prevent security gaps?
– we should implement access control at both the application and server levels,
– enforce the principle of least privilege,
– thoroughly test access control.
A02:2021-Cryptographic Failures
This vulnerability occurs when sensitive data such as sensitive data exposure (passwords, credit card numbers, or personal information) is inadequately protected and exposed to unauthorized users.
How do we prevent security gaps?
– Use encryption,
– Use secure transmission protocols (such as HTTPS),
– use appropriate access control.
A03:2021-Injection attacks
SQL injection vulnerabilities occur when untrusted data is sent to an interpreter as part of a command or query. Attackers exploit these vulnerabilities to execute malicious SQL commands, gain unauthorized access to databases, and manipulate or extract sensitive data.
How do we prevent security gaps?
– Use strictly parameterized queries,
– Comply with input validation and storage procedures.
A04:2021-Insecure Design
This is a new focus on the security risks often associated with design flaws. The best implementation will not secure a design if methods to protect against specific attacks have not been implemented beforehand.
How do we prevent security gaps?
- Model the risks,
- Follow secure design patterns and principles.
A05:2021-Security Misconfiguration
Another vulnerability stems from misconfigured security settings, such as default passwords, unnecessary services, or overly permissive access controls. Attackers exploit these misconfigurations to gain unauthorized access, escalate privileges, or compromise systems.
How to prevent risks?
- Conduct regular safety assessments,
- Implement automated configuration management tools.
A06:2021-Vulnerable and Outdated Components
Many web applications rely on libraries, frameworks, or third-party components that may contain security vulnerabilities. An attacker can exploit these vulnerabilities to gain unauthorized access or execute arbitrary code.
How to prevent them?
- Update the software regularly,
- Monitor for safety,
- Use software composition analysis tools to identify and fix vulnerabilities in third-party components.
A07:2021-Identification and Authentication Failure
Authentication vulnerabilities allow attackers to crack user accounts, passwords, session tokens, or keys. Typical identification failures include weak passwords, session fixes, other identification and authentication failures and inadequate authentication mechanisms.
Mitigation strategies include:
- Implementing secure authentication methods,
- Enforcing strong password policies,
- Enabling multifactor authentication
- Regularly update session tokens.
A08:2021-Software and Data Integrity Failures
This vulnerability refers to the risk of unauthorized or unintended changes to software or data, which can lead to serious data integrity failures or breaches. When software or data integrity fails, attackers can tamper with or modify the system, resulting in potential security breaches, data corruption, or loss of trust in the system.
Security assessments demand a multi-faceted approach, including:
- Implementing robust access controls and authentication mechanisms to restrict unauthorized access to sensitive data and system resources.
- Employing encryption and hashing techniques to protect data at rest and in transit, ensuring that data remains confidential and tamper-proof.
- Implementing secure coding practices, such as input validation and output encoding, to prevent injection attacks and other forms of data manipulation.
- Regularly audit and monitor system logs for suspicious activities or unauthorized modifications, enabling timely detection and response to security incidents.
- Keeping software and infrastructure components up-to-date with security patches and updates to address known vulnerabilities and reduce the risk of exploitation.
A09:2021-Security Logging and Monitoring Failures
This vulnerability pertains to deficiencies in an application’s ability to adequately log security-related events and failures and the failure to monitor these logs effectively. Security logging and monitoring are critical components of any robust security strategy, as they provide visibility into the activities occurring within an application or system, allowing for the timely detection and response to security incidents.
Mitigation strategies include:
- Defining a logging strategy that identifies which security events should be logged and the level of detail required for each event.
- Implementing logging mechanisms within the application or infrastructure components to capture relevant security events, such as authentication failures, access control violations, and anomalous activities.
- Centralizing logs in a secure location and implementing appropriate access controls to prevent unauthorized access or tampering.
- Employing log analysis tools and techniques to identify patterns, anomalies, or indicators of compromise within the logs.
- Establishing incident response procedures that outline the steps to be taken in the event of a security incident, including how to analyze logs, escalate alerts, and mitigate threats effectively.
A10:2021-Server-Side Request Forgery
This vulnerability occurs when an attacker manipulates a server to perform malicious requests on its behalf. This vulnerability allows attackers to interact with internal systems or perform actions that the server would normally have access to, leading to unauthorized data access, server-side privilege escalation, and even remote code execution.
Mitigation strategies include:
- Implement strict input validation,
- Cleansing URLs provided by users
- Restricting server capabilities to access sensitive resources
- The use of network-level security, such as firewalls and segmentation
OWASP recommendations for secure apps
The OWASP organization provides a comprehensive set of recommendations for application and security practices. These recommendations serve as guidelines for developers to create secure applications. These practices cover various aspects, including:
- Regular software updates and patches can prevent potential security breaches.
- Using secure coding libraries and frameworks, which have been tested for security.
- Thorough testing to identify and repair security vulnerabilities. This includes both automated testing and manual testing.
- Adoption of OWASP security standards and guidelines
Summary
In conclusion, OWASP provides invaluable support for ensuring software security. If we understand and properly implement the recommendations in the top 10 threats list and follow safe practices, we can clearly reduce the risk of security breaches and protect valuable data.
Of course, the road to secure software coding does not end with the OWASP Top 10. It is an ongoing process that requires regular updates, continuous learning, and diligent application of best practices. If you would like to learn more about how we ensure the security of all the components and applications we deploy, please contact us; we will be happy to share our experience and advise you on the right solutions.