Table of Contents
What are the most common concerns about moving to the cloud?
Companies may feel uncertain about migrating to the cloud due to concerns about whether entrusting data to a third-party provider will expose sensitive data to the risk of loss, potential breaches, or unauthorized access.What else could affect the delay of the migration process?
1. Lack of control When companies migrate their data and applications to the cloud, they relinquish some control over their infrastructure. Such a loss causes organizations concern, as they feel less able to effectively manage and monitor their data and access it for a specific group of users. 2. Conflict with GDPR When choosing a cloud provider, companies should know if the provider maintains server locations outside the EU or in the US. If there are cloud servers in the US, the US government gains access to data stored in the cloud upon request through the “CLOUD Act.” The transfer of personal data to US authorities under this act contradicts regulations under the General Data Protection Regulation (GDPR). This leads to problems for companies, as Article 82 of the GDPR gives the right to take action against the person responsible and the data processor in such a case. 3. Business disruption Cloud service failures or outages can affect business operations, leading to potential disruptions and financial losses. Companies often have complex IT environments with legacy systems and applications in place. Migrating these systems to the cloud and ensuring seamless integration can be complex and time-consuming. 4. Costs While cloud services offer scalability and cost-saving benefits, there may be concerns about the overall cost of migrating to the cloud and ongoing operational expenses. Companies are often concerned about unforeseen expenses such as price increases or the difficulty of accurately estimating usage and service costs. 5. 24/7 availability Access to company data must be guaranteed around the clock. A secure cloud means that all systems and networks involved must be fault-tolerant.What are the cloud security risks?
The cloud is just as secure, if not more so, than a hard drive, physical server, or data center. This is because data stored in the cloud is usually encrypted. In addition, big cloud computing companies have hired some of the world’s best data security experts to store data in multiple locations in case of a hardware failure or a security breach as part of the system. Most of the largest data breaches have involved traditional software on local servers, not data stored in the cloud. However, no security system is foolproof. Hence, uploading files to the cloud that has been unknowingly infected with malware can compromise stored data and significantly increase the risk of infecting the device used to access the data.Some of the most commonly cloud security vulnerabilities include:
- Data breaches: Cloud service providers store sensitive data for many customers, making them attractive targets for cybercriminals. A breach can cause the disclosure of sensitive information, financial losses, and damage a company’s reputation.
- Unsecured APIs: If they are poorly designed or have security holes, attackers can exploit them to gain unauthorized access to data and services.
- Insider Threats: Employees, contractors, or others with access to cloud infrastructure may inadvertently or maliciously compromise data or systems.
- Misconfiguration: Incorrectly configured cloud resources such as storage, databases, or access control settings can cause security vulnerabilities.
- Denial of Service (DoS) attacks: Cloud services can be the target of DoS attacks aimed at overloading the infrastructure and preventing legitimate users from using the services.
- Shared security responsibility: If multiple customers share the same hardware and software resources, this increases the risk of one tenant’s security breach affecting the security and performance of others using the same infrastructure.
Why is cloud security important?
Remember that cloud technology is rapidly evolving, and new security threats are emerging. Today, cybercriminals are improving their attack techniques, such as multifactor authentication. To effectively detect, investigate and respond to malicious activity, it is critical to stay ahead of attacks through thorough threat analysis. Organizations must assess their cloud environments regularly, adopt best practices, and stay on top of the latest security developments and threats. Let’s now discuss the most important practices for ensuring security.Three areas of cloud security assurance
Data security
To ensure the security of sensitive data, it is important to adequately protect it from unauthorized access, modification, and deletion. Securing transmission paths includes encrypting data and tracking its flow. A report conducted by TUV showed that when it comes to cloud security, 39% of companies are thinking specifically about encrypted data transmission to and from the cloud provider. Among companies with fewer than 500 employees, the percentage rises to 41 percent. Comparably, among companies with more employees, only 38 percent stress the importance of data encryption. Let’s take a closer look at how encryption affects security:- Data transmission
- Server-side data
- Client-side data
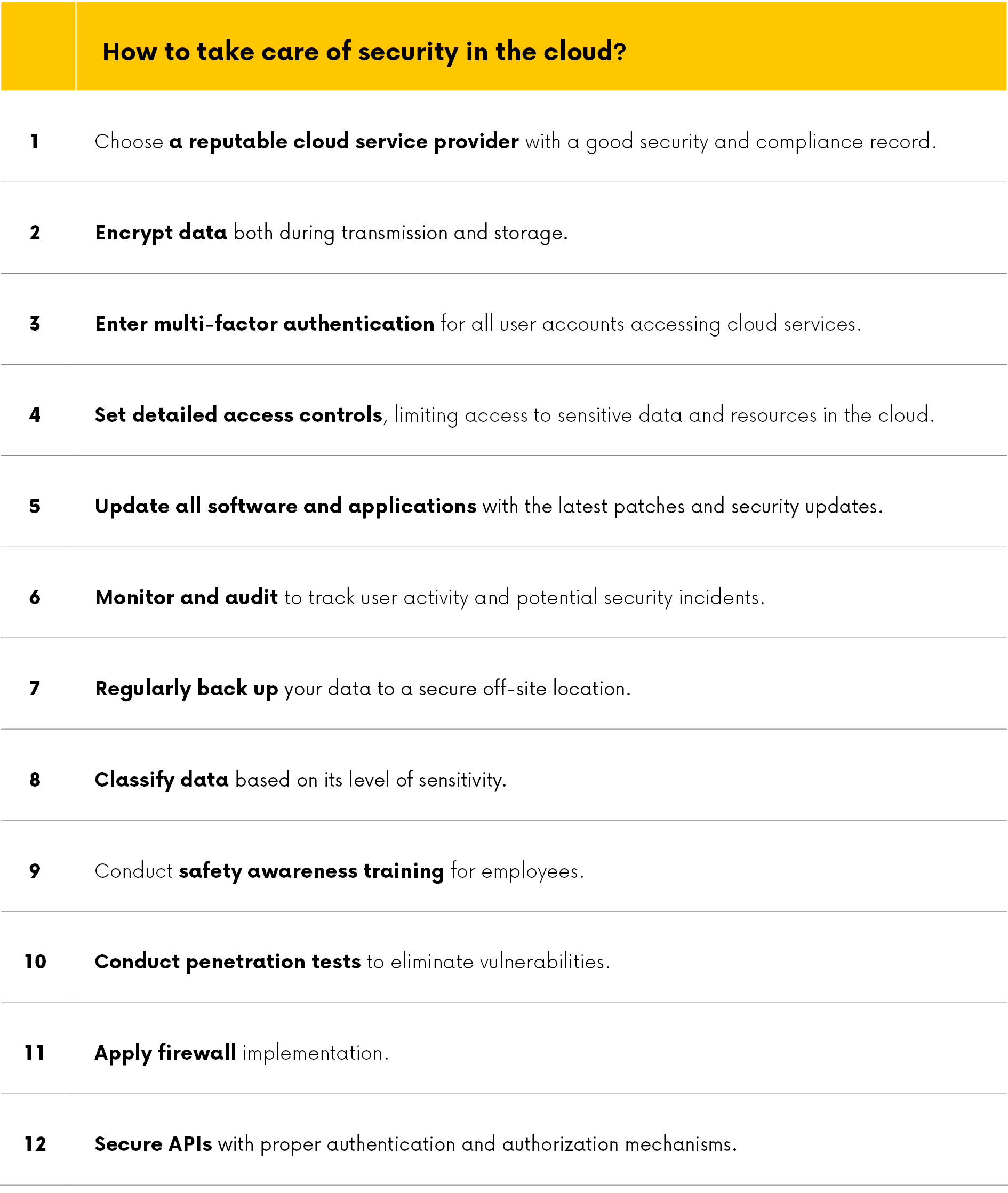
Identity and access management
Systems should be designed to provide access only to authorized individuals. Roles should also be configured to ensure that permission to modify or delete data is limited to appropriate users. This requires appropriate privilege restrictions and the use of encryption to limit readability. Similarly, administrator credentials and encryption keys must be protected to maintain these restrictions.Server location and legal compliance
Server locations within the EU primarily characterize the most secure clouds, as they are subject to strict DSGVO data protection guidelines. Caution should be exercised for cloud services located outside Europe. These services have much lower data protection requirements. The server’s location is closely related to compliance with relevant laws and regulations that apply to data, such as the GDPR Directive on the protection of the personal data of EU citizens. Generally, the data protection laws of the country where the server is located apply. Therefore, cloud service providers that advertise “hosting in Germany” are subject to strict German data protection laws. These companies include Deutsche Telekom, hosting provider STRATO, and smaller cloud companies such as CenterDevice. For other companies that offer “EU hosting,” data protection guidelines 95/46/EC and 2002/58/EC apply here. EU countries also have their own data protection laws. Regarding cloud services, Amazon (AWS) and Azure have subsidiaries in Germany; for example, Amazon currently operates three data centers in Europe: Frankfurt, London, and Dublin. Corporations can store their data only on European servers and not transfer it across the United States or other countries.Who is responsible for data security in the cloud?
Today’s modern cloud is highly secure and reliable, providing the cloud service provider (CSP) has a comprehensive, robust security strategy to protect against risks and threats. Larger cloud-based companies have the resources to maintain security measures throughout their IT environment and update them. This resource-intensive undertaking often overwhelms small and medium-sized companies. Nevertheless, it is vital to remember that the cloud provider is only partially responsible for data security. Security in the cloud is subject to a shared responsibility model, which means both ISPs and their customers should handle it.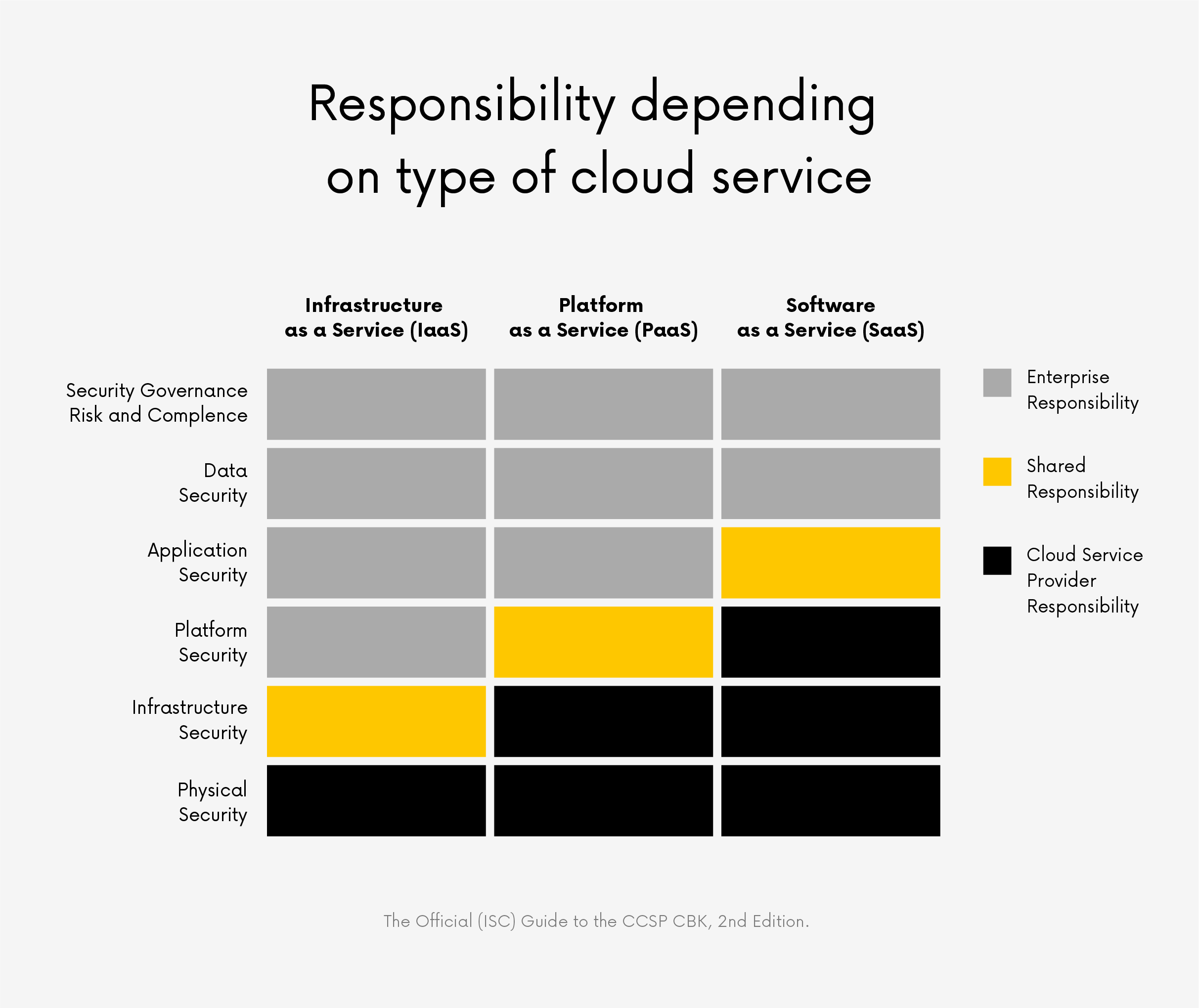 Depending on the model, i.e., IaaS, PaaS, or SaaS, the vendor and the company share responsibility for the secure operation of individual applications and application protection.
Depending on the model, i.e., IaaS, PaaS, or SaaS, the vendor and the company share responsibility for the secure operation of individual applications and application protection.
Cloud services are divided into the following models:
- Infrastructure-as-a-Service (IaaS) – In this model, the vendor provides the infrastructure for the company user to install and use software, such as an operating system or application.
- Platform as a Service (PaaS) – The provider provides and manages the hardware and software platform. The user company organizes the applications on the platform and protects the applications and data.
- Software-as-a-Service (SaaS) – the provider offers entire applications as cloud services in this model. The user’s company does not have access to the infrastructure and platform and has, at most, limited individual backup options.
Summary
While cybersecurity challenges remain ubiquitous for companies today, organizations are not defenseless against the dangers lurking in this sphere. The most important thing is regular analysis to recognize the threat and raise their own level of security. This includes both technical and organizational measures. If an enterprise prioritizes ensuring cloud security, it will undoubtedly protect itself from sophisticated cyberattacks that change over time. Do you need an experienced software security partner? Get in touch with our engineers. They will be happy to help develop vendor-independent and vendor-specific cloud security concepts for you. Sources:- secunet.com – Cybersecurity alliance.
- Federal Office for Security in Information Technology (BSI).
- Germany safe online – DSiN blog.